X.509 certificates are used to authenticate clients and servers. The mostcommon use case is for web servers using HTTPS.
No, according to their API private applications do not use the secret key for signing. You must generate an RSA public/private pair (one time event). Then upload your public certificate to their server. They will use it to verify your requests were signed by you and not someone else. Then you use your private key to sign all requests using RSA. I have read all about asymmetric encryption in PHP. I understand the mcrypt method. I understand the requirement of having two keys (Public and Private). The only thing I could not understand that where and how I generate these key pairs? Can anyone please explain the process of key generation?
To use asymmetric encryption, first generate private-public key pairs for each user authorized to have access to the server. Each authorized user's public key is stored on the server; each user's private key is encrypted and stored on that user's computer. Craftbukkit 1.7.10 download mac.
Creating a Certificate Signing Request (CSR)¶
When obtaining a certificate from a certificate authority (CA), the usualflow is:
- You generate a private/public key pair.
- You create a request for a certificate, which is signed by your key (toprove that you own that key).
- You give your CSR to a CA (but not the private key).
- The CA validates that you own the resource (e.g. domain) you want acertificate for.
- The CA gives you a certificate, signed by them, which identifies your publickey, and the resource you are authenticated for.
- You configure your server to use that certificate, combined with yourprivate key, to server traffic.
If you want to obtain a certificate from a typical commercial CA, here’s how.First, you’ll need to generate a private key, we’ll generate an RSA key (theseare the most common types of keys on the web right now):
If you’ve already generated a key you can load it withload_pem_private_key().
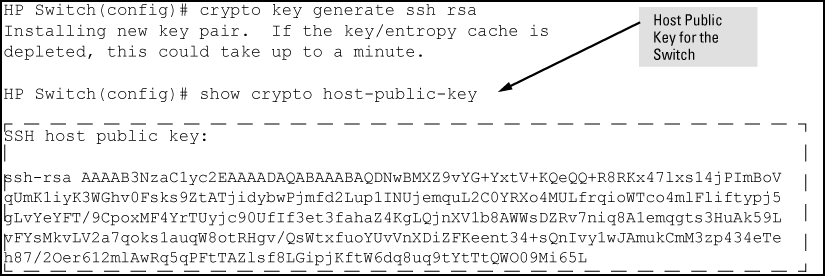
Next we need to generate a certificate signing request. A typical CSR containsa few details:
- Information about our public key (including a signature of the entire body).
- Information about who we are.
- Information about what domains this certificate is for.
Now we can give our CSR to a CA, who will give a certificate to us in return.
Creating a self-signed certificate¶
While most of the time you want a certificate that has been signed by someoneelse (i.e. a certificate authority), so that trust is established, sometimesyou want to create a self-signed certificate. Self-signed certificates are notissued by a certificate authority, but instead they are signed by the privatekey corresponding to the public key they embed.
This means that other people don’t trust these certificates, but it also meansthey can be issued very easily. In general the only use case for a self-signedcertificate is local testing, where you don’t need anyone else to trust yourcertificate.
Like generating a CSR, we start with creating a new private key:
Then we generate the certificate itself:
Microsoft powerpoint 2010 activation key generator download. Without a doubt, Microsoft Office Professional is acceptable for any user. For the very first period, we see the way the new variant consumes fewer resources often. Microsoft Office Professional Plus 2010 is an excellent addition related to the former edition. Then you may save the document on the internet and keep editing it in your home or from another computer. Word 2010, is much more stable and fast compared to previous versions of Microsoft Office also provides the option to access files from any computer because of its new online rescue option.
And now we have a private key and certificate that can be used for localtesting.
Determining Certificate or Certificate Signing Request Key Type¶

Certificates and certificate signing requests can be issued with multiplekey types. You can determine what the key type is by using isinstancechecks:
Returns the updated struct. If a structure does not exist, ColdFusion throws an exception. If a key exists and
Coldfusion Generate Private Public Key Pair Chart
See also
Structure functions; Modifying a ColdFusion XML object in the Developing ColdFusion Applications
Coldfusion Generate Private Public Key Pair Linux
History
ColdFusion (2018 release): Returns the updated struct.
ColdFusion MX: Changed behavior: this function can be used on XML objects.
Coldfusion Generate Private Public Key Pair 2017
Parameter | Description |
|---|---|
structure And you can use the 'Mood Tuner' of the Spotify party to adjust the atmosphere. If you are using mobile apps, you can also adjust the. Spotify 3rd party dj app. It will mix Spotify songs automatically just like a professional human DJ. Adobe creative suite 5 master collection key generator. We are continually making additional tools and information available online in order to provide you with flexible options for resolving issues as fast as possible.If you are having any issues with installing or uninstalling any of your Creative Suite 5 applications, please try rebooting your system prior to contacting Support. Alternatively, you can click on Change beside the country name at the top of the screen to select a different country or region.Free troubleshooting resources include, and more. If you require technical assistance for your product, including information on complimentary and fee-based support plans and troubleshooting resources, more information is available at. Outside of North America, go to, click on the drop down menu under the question “Need a different country or region?”, choose a different country or region, then click GO. | Structure to contain the new key-value pair. |
key | Key that contains the inserted value. Franklin gothic heavy condensed. |
value Is kodi safe for mac. Jul 06, 2018 Finding and Installing Kodi Add-ons for Mac. All of Kodi’s add-ons can be divided into two rough categories: official and unofficial. The former includes dozens of add-ons packaged into a single repository tested and approved by the Kodi development team. | Value to add. But, there is no clear idea about the infections on the dead people. However, the most important change that you will see is, an Ellie is a primary playable character in the gameplay not like as a Joel.How the Last of Us 2 games will end?While coming to the end of the Last of Us game, Joel will save the Ellie for the sake of cure and as well as eliminates the beating of the virus. When the Joel takes his brother to the wilderness camp, Joel will immediately lie to the Ellie in the gameplay. The last of us pc cd key generator 2020. Jan 15, 2020 You can use Hide My IP License Key Generator with new tools. As a result of hackers can use your IP deal with to get plenty of details about you and may hack your units. Due to this fact, they will additionally publish bloggers on your laptop. With this keylogger, they will steal your login data. Feb 23, 2020 Hide My IP 6 License Key Generator also provides the private as well as enterprise solutions to keep you safe online. You can also connect to a VPN on a server in your home country during the traveling abroad. In short, a VPN is a way to increase and better your privacy and security by connecting to the internet on a server of your choosing one. Hide my ip 6 licence key generator. Hide My IP Keygen is a powerful and approachable application you can use to make your IP address anonymous when connecting to the Internet, by switching to a fake one. This way, you can protect your real identity from hijackers, as well as lift bans on content blocked due to geographical restrictions. It has advanced settings. |
allowoverwrite | Optional. Whether to allow overwriting a key. The default value is False. Civilization 5 mac download free full version. |